KeePass – CVE-2023-32784 – POC
〰️
KeePass – CVE-2023-32784 – POC 〰️
Password Managers are excellent. They help have random secure passwords for each account, they encourage good password hygiene and enforce the latest encryption standards. But how good is encryption when an exploit like CVE-2023-32784 is discovered…? Well, still amazing – Unless the attacker has access to your machine… or a process dump… or a memory dump… or a swap file (pagefile.sys)… or the hibernation file (hiberfil.sys). That being said, if a malicious actor had those files available and access to the password database file, you may have other concerns.
Password managers are still a safe, secure method however, as with any technology, exploits can and do happen. Exploits like these give password managers a bad name and scaremonger end users.
CVE-2023-32784:
In KeePass 2.x before 2.54, it is possible to recover the cleartext master password from a memory dump, even when a workspace is locked or no longer running. The memory dump can be a KeePass process dump, swap file (pagefile.sys), hibernation file (hiberfil.sys), or RAM dump of the entire system. The first character cannot be recovered. In 2.54, there is different API usage and/or random string insertion for mitigation.
The developer has acknowledge the vulnerability and has attempted mitigations. You can see the initial forum post and the information addressed here:
https://sourceforge.net/p/keepass/discussion/329220/thread/f3438e6283/?limit=25#65fb/ccca
This vulnerability is still awaiting analysis and thus, has no CVSS score.
PROOF OF CONCEPT (POC)

It’s worth noting, due to the way the vulnerability works, it is impossible to know the first character of the master password however, this is trivial and can be bypassed through bruteforcing the first character if the password is randomly generated. If the password is a word/string, it is very easy to determine the first character such as in both examples I will provide below.
On another note, it’s worth mentioning the tool is not always 100% accurate. What I mean by this is that sometimes, depending on the length and the .dmp file you use, you may find one or two inconsistencies such as an undetermined missing character. That being said, I managed to gather the clear text master password on every test I tried.
Prerequisites
KeePass Master Password Dumper
STEPS
Step 1. Download and install .NET
Steps 2. Download and install KeePass
All current versions, 2.54 and before are affected.

Step 3. Download keepass-password-dumper from Github.
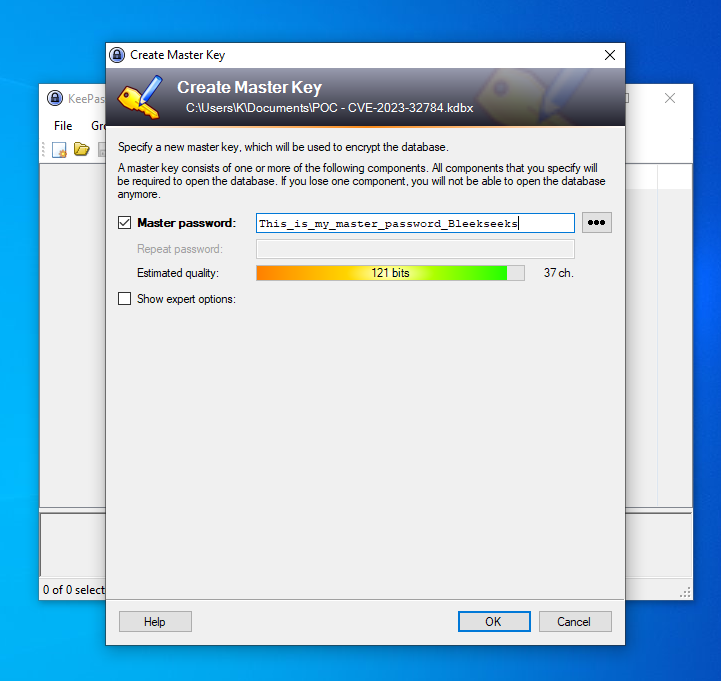
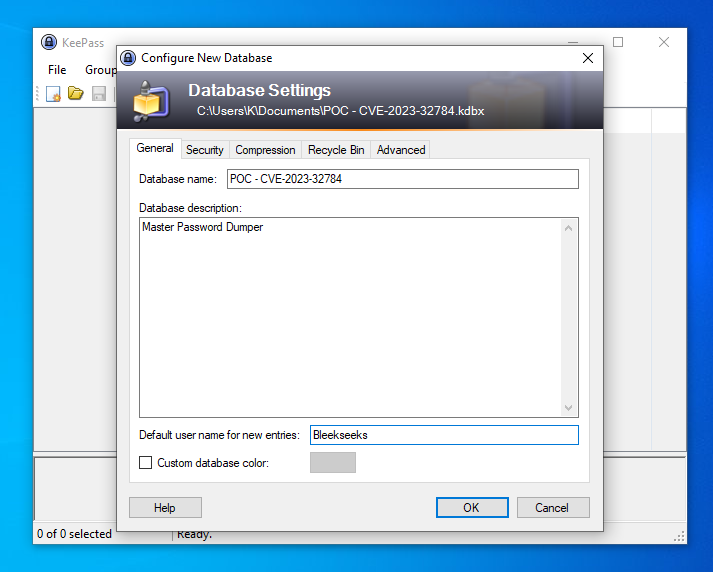
Step 4. Create a new password database within KeePass
Step 5. Open command prompt and change directory to the folder containing the Github file
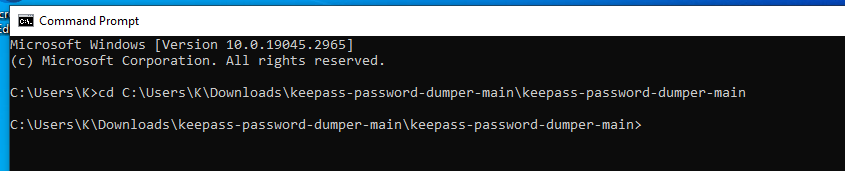
Step 6. We need a .dmp/log file to analyse. This can be a KeePass process dump, swap file (pagefile.sys), hibernation file (hiberfil.sys), or RAM dump of the entire system. The easiest file to obtain for the POC is to complete a process dump for KeePass.
We can do this by opening KeePasss, then right clicking the process in Task Manager and clicking ‘Create dump file’.
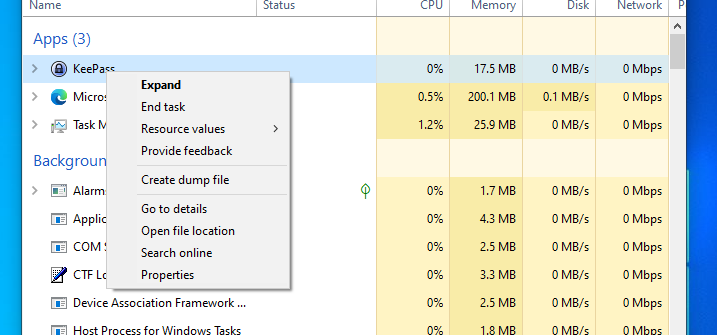
By default, the dump file will be located C:\Users\USER PROFILE\AppData\Local\Temp\KeePass.dmp
Process dump – C:\Users\USER PROFILE\AppData\Local\Temp\xxxx
Memory dump – if you would like to do a memory dump, I would recommend downloading the NotMyFault tool located here: https://download.sysinternals.com/files/NotMyFault.zip. Once downloaded, you can manually create a .dmp file by crashing your machine
swap file (pagefile.sys) – is located on your local storage drive (C:), but it’s hidden by default since it’s an important system file. That means you’ll have to reveal it in Folder Options
hibernation file (hiberfil.sys) – The Hiberfil.sys hidden system file is located in the root folder of the drive where the operating system is installed.
Step 7. From the location we browsed to in step 5. run the following in command prompt: dotnet run PATH_TO_DUMP
For our example, we will be running: dotnet run C:\Users\USER PROFILE\AppData\Local\Temp\KeePass.dmp
![]()
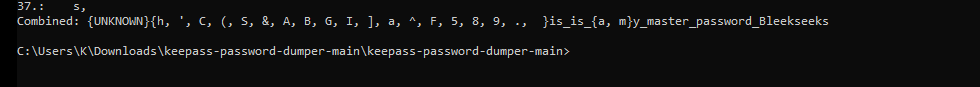
So the password was: This_is_my_master_password_Bleekseeks
As said above, the first character will always be missing. Out of all my tests, this was probably the one that was the least accurate and even so, it would be an easy job to ascertain the password via simple guesswork or some minor bruteforcing.
One of my other tests, the password was: “Bleekseeks_is_my_password” Below is the result from the process dump:
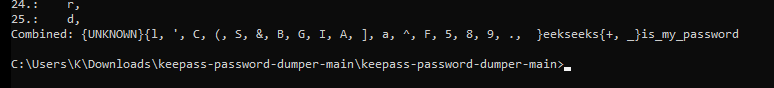
Here is another example. You can make out the second character to be one of the the letters listed below (e, N, c, d, f, g, W, 1), the answer logically being ‘e’ to complete the word ‘Secret’.
The whole password can easily be determined to make out SecretMasterPassword

Conclusion
Due to the many vectors to gain the password there are a few steps that can be taken that will somewhat reduce the risk. If you use KeePass, you should change your master password, delete swap file (pagefile.sys), hibernation file (hiberfil.sys), remove prior memory dumps (usually caused by crashes), utilise full disk encryption and ensure old computers are securely wiped before being disposed.
The attacker would need access to your system in some form which is the main hurdle here and that being the major limiting factor. If a malicious actor has access, there are other tools such as KeeFarce which can easily be used instead of this exploit however, the key difference being this current CVE affects all current versions.
Regardless of mitigation and limiting factors, this is a serious vulnerability. If old KeePass databases are found, now or in future on a vulnerable system, there is a substantial risk to the integrity to the accounts stored and the data they hold. Some .dmps/.sys/.log files can remain for years which is a potential leak of previous and current KeePass master passwords.
