DeepFakes: How attackers are weaponising real-time face swapping
Deepfakes have evolved from niche internet curiosities into real-world weapons. From fake job interviews andn romance schemes to impersonating public figures in crypto scams, Deep Fakes are only becoming more of a problem. This blog is designed to cover the tactics, real-world cases, and why seeing shouldn’t mean believing anymore.
EvilQR Phishing / QRLJacking
QR codes are designed for usability, not security. Using QRLJacking, a victim can unknowingly grant access to their account by scanning a QR code.
KeePass Master Password Exploit – CVE-2023-32784 – Proof Of Concept (POC)
Another day, another CVE. It is possible to recover the master password in cleartext for KeePass. Write up, examples and a POC to demonstrate CVE-2023-32784
How to check Shared mailbox’s Access Rights via Powershell
How to check Shared mailbox’s Access Rights via .csv with Powershell. Useful for checking permissions without having to go through the office.com admin/exchange interface.
NoVNC and Browser In The Browser Phishing attack POC/Explained
Combining two advanced phishing techniques
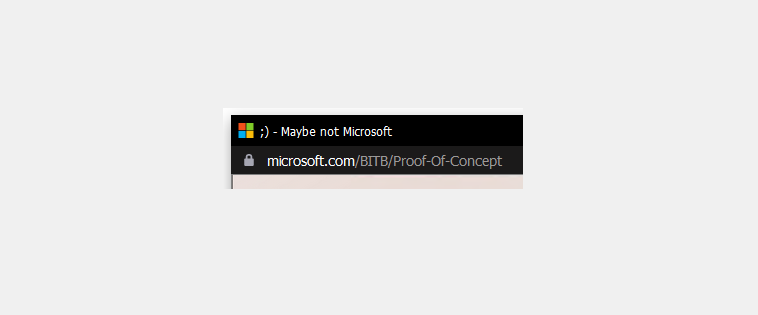
Browser In The Browser (BITB) Attack – POC
Browser In The Browser (BITB) phishing attacks are less common but very effective when used. They’re hard to identify and easy to setup!
My first BurpSuite Vulnerability using Intercept
My first time using BurpSuite Intercept and I found a vulnerability which allows me to change the price of items and checkout.
Force Outlook for Mobile via Conditional access
How to force mobile devices to use the Outlook App instead of their native apps.