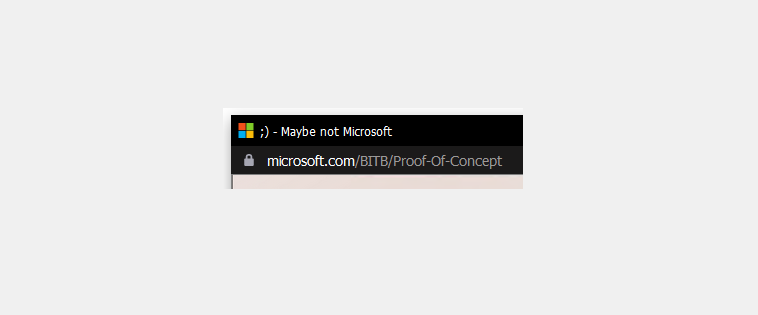
Introduction
A Browser In The Browser (BITB) phishing attack is a less common method used by malicious actors. By using BITB, it can allow the malicious actor to display content posing as a legitimate website including the same domain name and even the HTTPS secure padlock. Due to the way Javascript works, malicious actors can even make the hover over link display the imitated website. This makes it incredibly difficult to spot especially for end-users and can allow them to gather passwords and potentially certain Multi-factor authentication methods such as SMS.
By using mr.d0x’s template with a spoofed Microsoft login page, we’re able to setup a quick and easy proof of concept to imitate how it would look for the end-user.
mr.d0x’s write-up can be found here: https://mrd0x.com/browser-in-the-browser-phishing-attack/ and the templates used for this can be found here: https://github.com/mrd0x/BITB
I will also be using JoniRinta-Kahila’s fake Microsoft login to spoof Microsoft’s login page as seen here: https://github.com/JoniRinta-Kahila/microsoft-login-spoof and capture credentials.
Proof-Of-Concept (POC)
When downloading the templates, the first thing we see is the zip file which contains the following:

Next, we will need to open the index.html file via an editor of our choice.
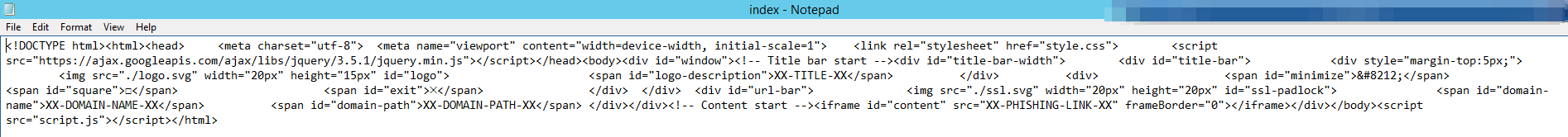
You may see a few oddities within this file, all beginning with XX-
These are the areas we need to edit, we will use the reference below to assist.
XX-TITLE-XX – The title that shows up for the page (e.g. Sign in to your account now)
XX-DOMAIN-NAME-XX – Domain name you’re masquerading as. (e.g. gmail.com)
XX-DOMAIN-PATH-XX – Domain path (e.g. /auth/google/login)
XX-PHISHING-LINK-XX – Phishing link which will be embedded into the iFrame (e.g. https://example.com)
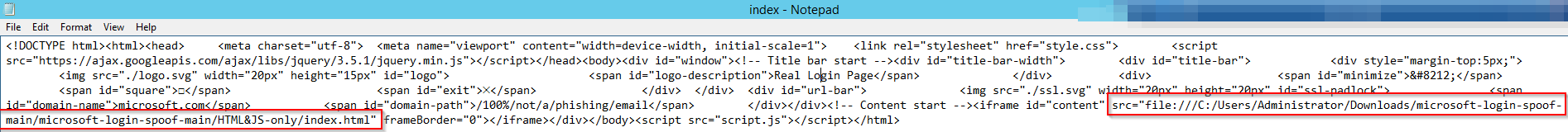
Below is how I have setup my config:
XX-TITLE-XX – Real Login Page
XX-DOMAIN-NAME-XX – microsoft.com
XX-DOMAIN-PATH-XX – /100%/not/a/phishing/email
XX-PHISHING-LINK-XX – C:\Users\Administrator\Downloads\microsoft-login-spoof-main.zip\microsoft-login-spoof-main\HTML&JS-only\index.html
I highlighted the XX-PHISHING-LINK-XX as typically this would be hosted on a site and would be a web address but as I am testing this POC, I decided to just use the spoofed Office 365 login on my local machine. The end result will be almost identical.
Now it’s time to see how it looks with our current setup, to do this we need to open the .html file with a web browser, as seen below

Not bad! Excluding the white background (that wouldn’t be there in a real attack) it would be almost impossible to be able to tell it’s not a legitimate sign-in window especially considering the domain is correct and the site has an secure padlock. The average user and probably even a more advanced user is likely to fall victim to this kind of attack. This can lead to MFA bypass depending on the type of authentication used.

With some minor tweaks, you can easily make the page look considerably more legitimate by using a title and domain path that doesn’t look out of place.
Conclusion
This whole POC has taken me very little effort and probably less than an hour to setup. If it was a motivated phishing attack with real intent, it would look considerably better and would aim to capture user input with MFA SMS text codes or other potentially phishable MFA methods.